You’ve probably noticed that some Internet browsers like Firefox and Google Chrome now display verified company information to the left of an encrypted web address. This is an easy way to show that the website has an extended validation certificate, indicating that the site’s identity has been verified.
You’ve probably noticed that some Internet browsers like Firefox and Google Chrome now display verified company information to the left of an encrypted web address. This is an easy way to show that the website has an extended validation certificate, indicating that the site’s identity has been verified.
An extended validation (EV) certificate will not provide any additional encryption strength to a website. Instead, it shows a user that extensive verification of a website’s identity has already taken place.
How Web Browsers Show Extended Validation Certificates
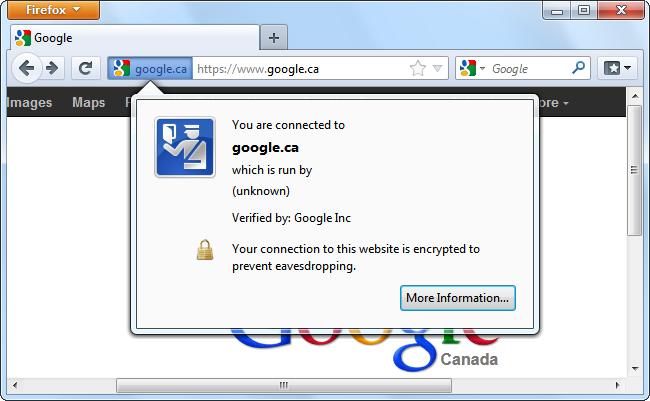
You’ll see on an encrypted website that doesn’t use an extended validation certificate, Mozilla Firefox indicates that the website is “run by unknown.”
Google Chrome won’t display anything special indicating that the website’s identity was verified by the certificate authority that issued the website’s certificate.
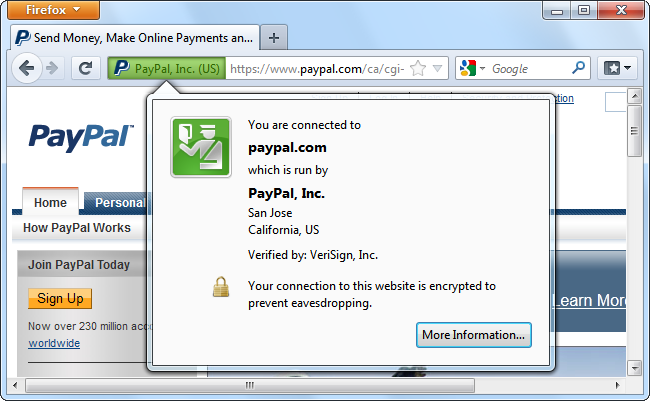
When you’re on a website that uses an EV certificate, Firefox let’s you know that’s operated by a specific organization, and that information has been verified. According to this dialog, VeriSign has verified that we’re connected to the real PayPal website, which is run by PayPal, Inc.
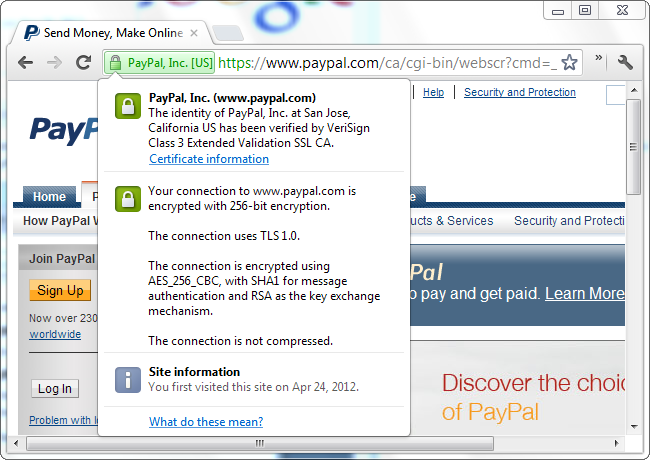
Then when you’re connected to a website that has an extended validation certificate in Google Chrome, the organization’s name appears in your address bar. The information dialog tells us that PayPal’s identity has been verified by VeriSign using an extended validation certificate.
SSL Certificate Troubles
Standard SSL certificates provide very little verification of a website’s identity. Many years ago, certificate authorities would verify a site’s identity before issuing a certificate. The certificate authority would check that the business requesting the certificate was fully registered, call the phone number, and verify that the company was a legitimate operation that matched its website.
Eventually, certificate authorities began offering “domain-only” certificates. These were a lot cheaper to get, as it was less work for the certificate authority to quickly check that the requester own a specific domain.
Phishers eventually figured out ways to take advantage of this. For example, a phisher could register the domain paypall.com and purchase a domain-only certificate. Whenever a user visited paypall.com, the web browser would display the standard lock icon, providing a false sense of security. Web browsers didn’t know the difference between a domain-only certificate and a certificate that involved the more extensive verification process of a website’s identity. As a result, public trust in certificate authorities to verify websites has fallen over the years.
This brings us to…
How EV Certificates are Different and Better
An extended validation certificate shows that a certificate authority has verified that a website is operated by a specific organization. For example, if a phisher tried to get an EV certificate for paypall.com, the request would be denied.
Unlike standard SSL certificates, only certificate authorities that pass an independent audit are permitted to issue EV certificates. The official Certification Authority/Browser Forum (CA/Browser Forum), a voluntary organization of certification authorities and browser vendors such as Mozilla, Google, Apple and Microsoft provide strict guidelines that all certificate authorities issuing EV certificates must abide by. This prevents certificate authorities from running another program where they utilize lenient verification practices to offer cheaper certificates.
The guidelines set by the committee demand that the certificate authorities verify the organization requesting the certificate is officially registered itself, that it owns the domain in question, and that the person requesting the certificate is in fact acting on behalf of the organization.
This involves checking through government records, contacting the domain’s owner, and contacting the organization to verify that the person requesting the certificate works for the organization. Extended validation certificates are, fundamentally, an attempt to restore public trust in certificate authorities and restore their role as gatekeepers against imposters and identity theft.